Version 1.680
Released: 2025-07-17
‼️ Sender address spoofing protection new custombuild
The Exim mail server configuration is extended to block user attempts to spoof the sender address. This is implemented as an additional Exim ACL for email submitted over SMTP. The ACL checks the username from the SMTP authentication against the sender address provided in the SMTP MAIL FROM command (also known as the envelope sender).
The general idea of sender address validation is to allow an email account to be able to send from any address as long as an email reply to the sender address would be routed back to the same email account.
Valid sender address examples:
- Main mailbox address is always allowed to be used as the sender address.
- Same address (local part) but a different domain is allowed to be used if the domain is an alias of the main address domain.
- Any forwarder email address can be used as a sender address if the forwarding rule is configured to deliver emails to the main address.
- Any unused email address in the same domain can be used by the mailboxes that are configured to be a catch-all mailbox for that particular domain.
The sender address spoofing protection is enabled by default. However, it can be explicitly disabled to stay backwards compatible with the old Exim configuration by setting the AUTH_BLOCK_SENDER_SPOOFING = no variable in the /etc/exim.variables.conf.custom file.
Examples:
# Disable sender address validation (insecure):
sed -i '/^AUTH_BLOCK_SENDER_SPOOFING /d' /etc/exim.variables.conf.custom
echo 'AUTH_BLOCK_SENDER_SPOOFING = no' >> /etc/exim.variables.conf.custom
da build exim_conf
# Restore sender address validation:
sed -i '/^AUTH_BLOCK_SENDER_SPOOFING /d' /etc/exim.variables.conf.custom
da build exim_conf
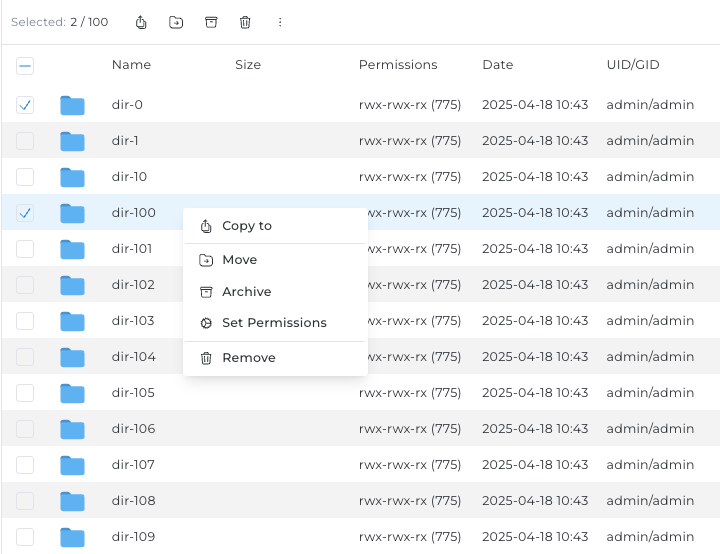
New File Manager's files and folders table design evolution update
The File Manager's files and folders table has been redesigned with a new design and optimized rendering logic, resulting in improved performance and a more streamlined user experience when browsing and managing files.
The layout is kept the same, ensuring that users can continue to navigate and interact with the File Manager as before.
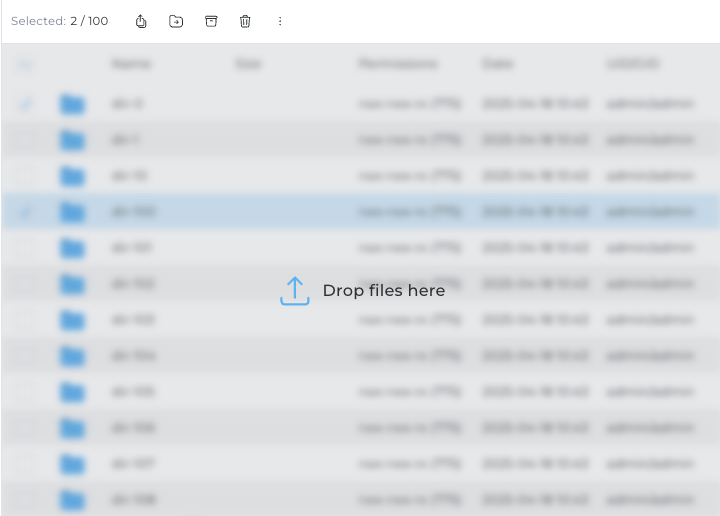
Improved drag and drop functionality in File Manager evolution update
The drag and drop functionality in the File Manager has been reworked for greater reliability and usability. Files and folders can now only be dropped onto the main files and folders table area, which immediately triggers the upload dialog for the dropped items. This change eliminates previous bugs and ensures a more consistent and predictable upload experience.
Software version changes custombuild update
apache2.4updated from2.4.63to2.4.65composerupdated from2.8.9to2.8.10litespeedupdated from6.3.3-1to6.3.3-2lz4 (PHP extension)updated from0.4.4to0.5.0modsecurity_owasp_rulesupdated from4.15.0to4.16.0modsecurityupdated from2.9.10to2.9.11nginxupdated from1.28.0to1.29.0PHP 8.1updated from8.1.32to8.1.33PHP 8.2updated from8.2.28to8.2.29PHP 8.3updated from8.3.22to8.3.23PHP 8.4updated from8.4.8to8.4.10redisupdated from8.0.2to8.0.3
Note:
Using apache2.4.64 together with nginx may require to enable passing of the server name through TLS Server Name Indication extension in nginx config when using ssl reverse proxy.
# Example for nginx_apache webserver
# When overriding Host header for SSL reverse proxy
proxy_pass https://example.com;
proxy_set_header Host $host;
proxy_ssl_name $host;
proxy_ssl_server_name on;
See proxy_ssl_server_name and proxy_ssl_name.
Wildcard options are not preselected evolution fix
Ticking the "Wildcard" option (found within admin level -> Account Manager -> SSL Certificates -> Get automatic certificate from ACME Provider) previously did not preselect the required certificate entry options.
Removed cakey, cacert, carootcert configuration options from directadmin.conf removal
The location of server host name TLS certificate files can no longer be customised. The files will always be stored in the default locations:
/usr/local/directadmin/conf/cakey.pem- server host name TLS key./usr/local/directadmin/conf/cacert.pem- server host name TLS certificate./usr/local/directadmin/conf/carootcert.pem- intermediate CA certificates.
On the servers where these options were set to non-default values, the certificate files will be automatically copied to the default location.
Removed surplus data from filemanager files search removal
Simplified files search in filemanager.
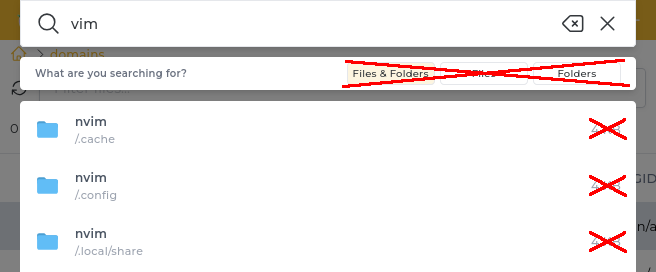
/CMD_FILE_MANAGER?action=recursive_search changes:
- Removed
typefilter - Returned files size is always zero
Removed leftover Userdir configuration from apache templates removal
The default IP apache vhost template is cleaned up by removing UserDir directives, previously used when userdir_access CB option, was enabled.
HAVE_USERDIR_ACCESS token is always 0
Removed column size menu customization option evolution removal
It is no longer possible to select how much space a menu category could take up.
Removed filtering from files and folders table evolution removal
The filtering feature of files and folders in the File Manager was removed.
